The Instructure Community will enter a read-only state on November 22, 2025 as we prepare to migrate to our new Community platform in early December.
Read our blog post for more info about this change.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Community
- Canvas
- Canvas Integration Documents
- Configuring Microsoft Entra ID (SAML) and Canvas A...
Options
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Configuring Microsoft Entra ID (SAML) and Canvas Authentication
Configuring Microsoft Entra ID (SAML) and Canvas Authentication
|
Official Canvas Document |
 |
Authentication Terminology
| Term | Definition |
|---|---|
| IdP |
Identity Provider The job of the IdP is to identify users based on credentials. The IdP typically provides the login screen interface and presents information about the authenticated user to service providers after successful authentication. Microsoft Entra ID is the Identity Provider. |
| login_id |
Username in Canvas terminology. When information about an authenticated user is returned to Canvas, a user with a login_id matching the incoming data is looked for. |
| Metadata |
Information about the SP or IdP. This metadata is almost always provided in the form of XML. The metadata about your Canvas instance is located at https://<YOURDOMAIN>.instructure.com/saml2 (replace <YOURDOMAIN> with the first portion of your Canvas domain). |
| SAML |
Security Assertion Markup Language |
| SIS | Student Information System |
| SIS ID |
Unique ID of a user in Canvas. Used to link a user to an outside system, often a Student Information System (SIS). |
| SLO |
Single Logout When a user logs out of a service, some IdPs can subsequently log the user out of all other services the user has authenticated to. Microsoft Entra ID supports this but may occasionally experience issues such as preventing a successful logout. Users will be logged out of Canvas but may not be logged out of Microsoft Entra ID. |
| SP |
Service Provider An SP is usually a website providing information, tools, reports, etc to the end user. Canvas provides a learning environment to teachers, students, and admins and is, therefore, the Service Provider. Note: An SP cannot authenticate against an IdP unless the IdP is known to the SP. Likewise, an IdP will not send assertions to an SP that it does now know about. |
| SSO |
Single Sign-On This is what happens when a user isn't required to log in to a second service because information about the authenticated user is passed to the service. |
Pre-requisites
- Canvas does not automatically create user accounts from successful single-sign-ons. User accounts must either be created manually in the web interface or through the SIS import CSVs.
- The login_id field in Canvas must match the selected field returned from Microsoft Entra ID.
- Your organization must have a Microsoft Entra ID subscription.
- You must be able to log in to the admin console for your organization.
- Referencing of <YOURDOMAIN> in this guide is referring to your Canvas URL (ex: https://<YOURDOMAIN>.instructure.com would be https://institution.instructure.com)
Login Release Valve
You may accidentally lock yourself out of Canvas while you are setting up authentication. If this happens, you can log in to Canvas using local authentication. Simply go to https://<YOURDOMAIN>.instructure.com/login/canvas (This forces Canvas to display the local login form rather than redirecting to the SAML login page).
Configure Microsoft Entra ID
To configure the integration of Canvas into Microsoft Entra ID you need to add Canvas from the gallery to your list of managed SaaS apps.
-
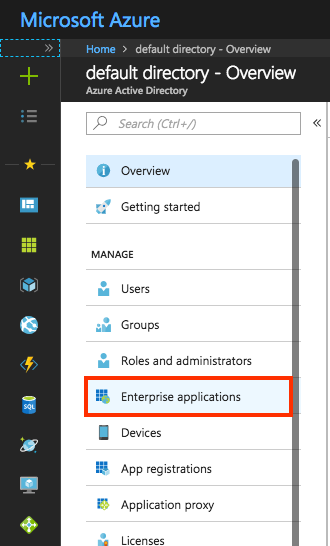
In the left navigation panel of the Azure portal, click Microsoft Entra ID icon.
-
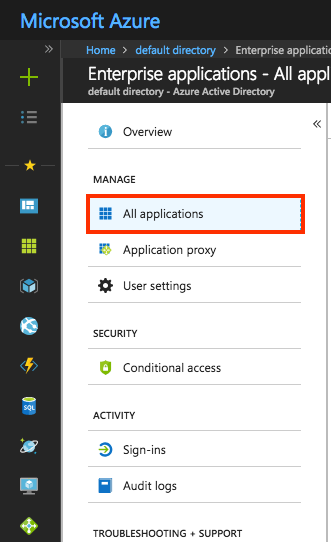
Click the Enterprise applications, then click All applications.
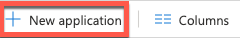
3. To add a new application, click the New application button at the top of the dialog.
4. In the search box, type Canvas [1]. In the results panel, select Canvas [2] and then click the Create button [3] to add the application.
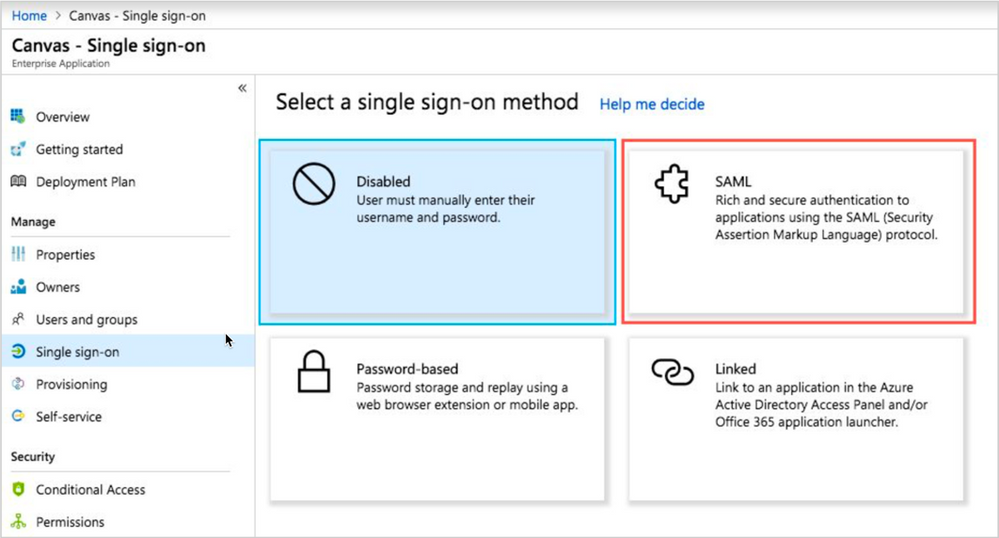
5. In the Canvas | Overview page of the Azure portal, click on Single Sign-on.
6. Click SAML.
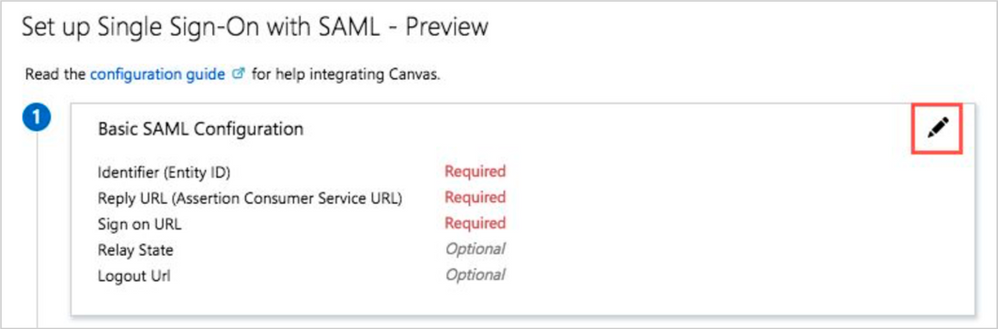
7. On the Set up Single Sign-On with SAML page, edit the Basic SAML Configuration section by clicking the pencil in the top-right corner.
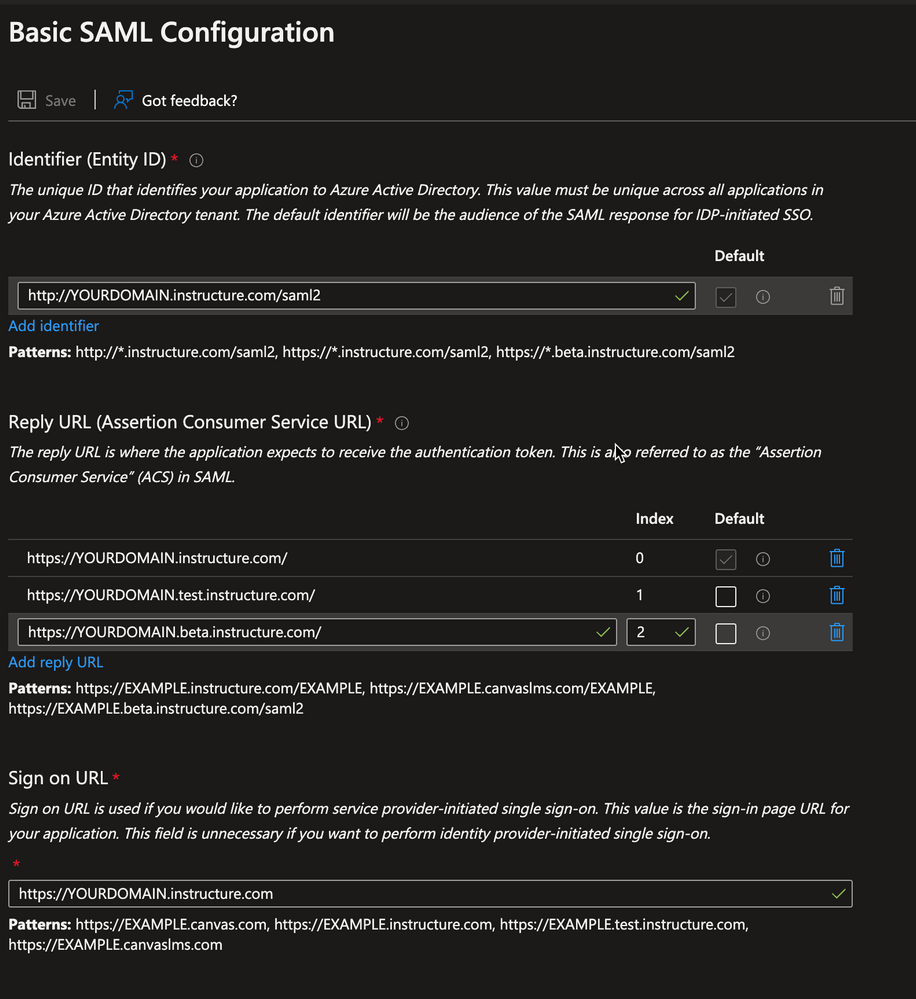
8. Click Add identifier and fill in the Identifier (Entity ID) fields with the Canvas Service Provier Entity ID. Be sure to use http (not https) , your canvas domain, followed by /saml2 (ie. http://<YOURDOMAIN>.instructure.com/saml2 ).
In the Reply URL (Assertion Consumer Service URL) fields, add your Canvas domains (production, test, and beta) (ie. https://<YOURDOMAIN>.instructure.com/* ). Click Add reply URL to create a new input. Examples below:
-
- https://<YOURDOMAIN>.instructure.com/
- Index: 0
- https://<YOURDOMAIN>.test.instructure.com/
- Index: 1
- https://<YOURDOMAIN>.beta.instructure.com/
- Index: 2
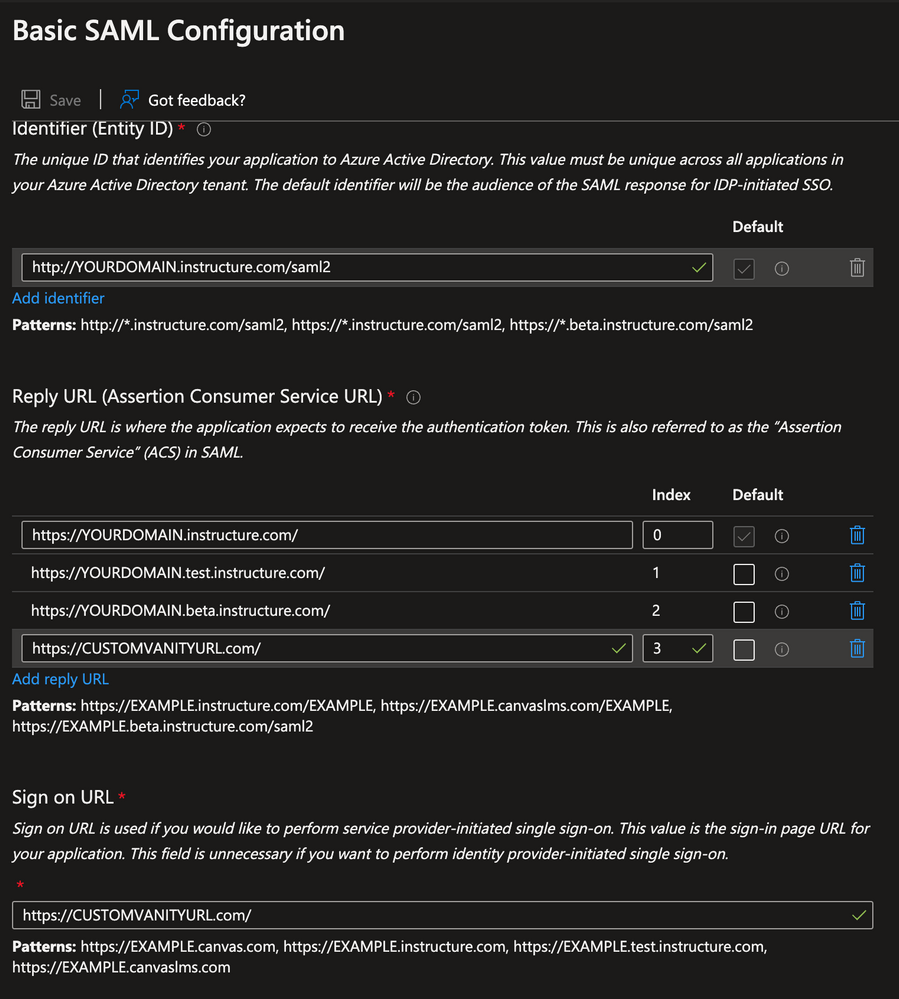
- https://CUSTOMVANITYURL.com/ - You will only use this value if you have a vanity URL with Canvas. If you do not, you will not need to include this value in your configuration.
- Index: 3 (if applicable)
- https://<YOURDOMAIN>.instructure.com/
In the Sign-on URL field, enter your Canvas production URL. This will be https://<YOURDOMAIN>.instructure.com or it will be https://<CUSTOMVANITYURL>.com if you have a vanity URL with Canvas.
Click Save in the top-left corner.
Here is an example if you use a normal Canvas domain:
Here is an example if you use a vanity URL with Canvas:
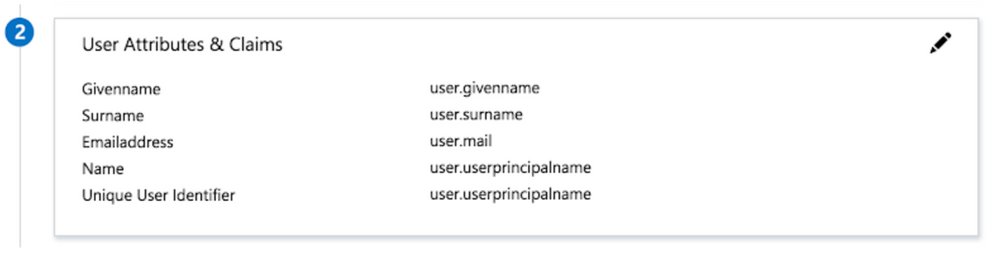
9. Edit the second section, User Attributes & Claims.
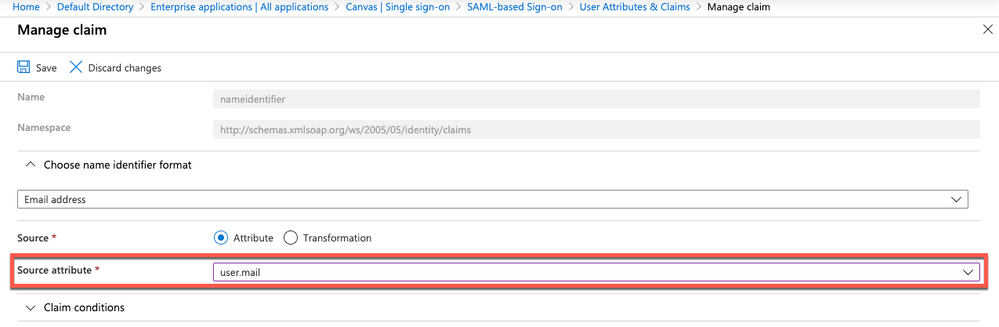
***NOTE: This guide walks through the steps of sending the email address as the identifier. If you do not wish to send the email address as the identifier, please select which identifier you would like to send.
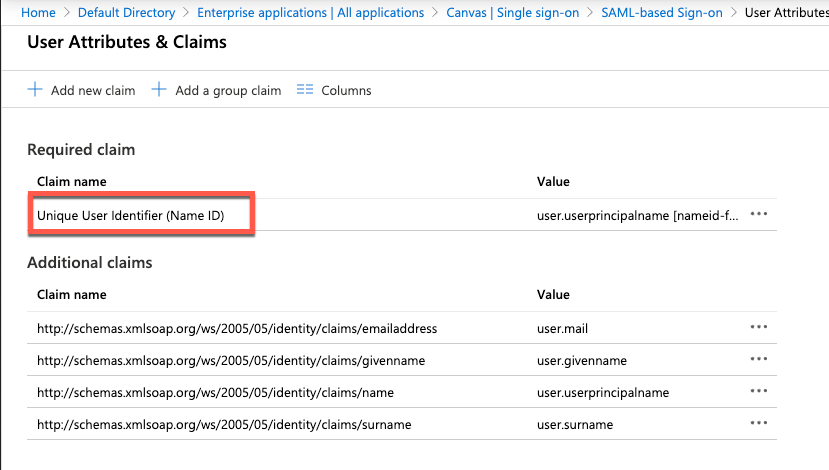
10. Click Unique User Identifier (Name ID) under required claim and change Source attribute to user.mail and click Save.
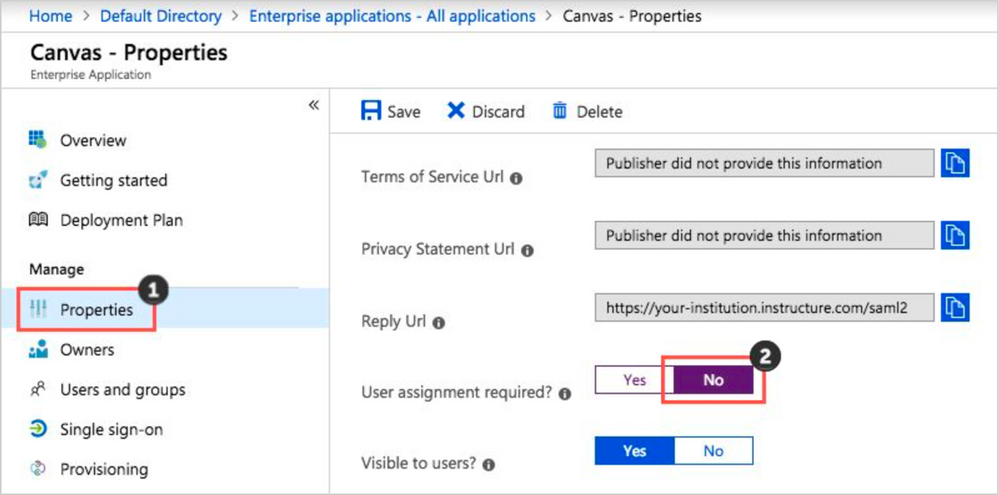
11. Click Properties [1]. Change User assignment required to No [2]. Click Save.
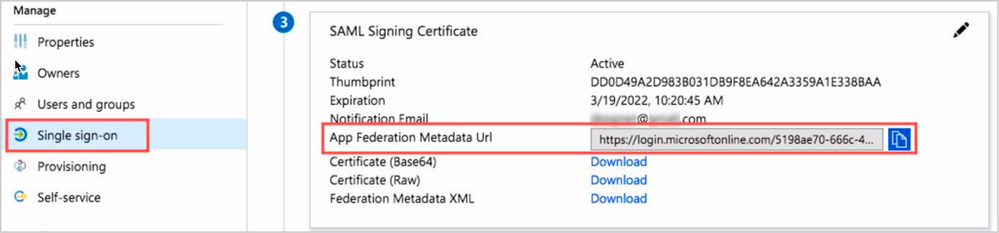
12. Return to the Single Sign-on screen. In the third section, copy the App Federation Metadata Url.
Configure Canvas Authentication
The following steps take place in Canvas (https://YOURDOMAIN.instructure.com).
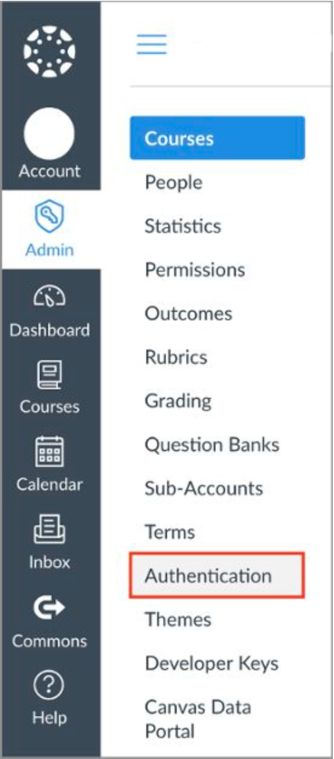
13. In a new browser tab, log in to your Canvas instance as an administrator. From the Admin tile, click Authentication.
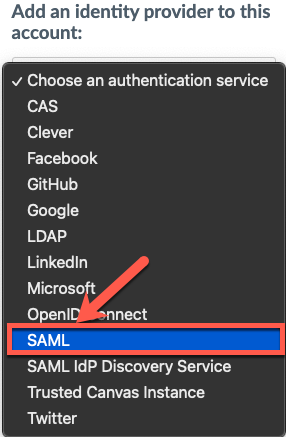
14. Click on the Choose an Authentication Service drop-down, then select SAML.
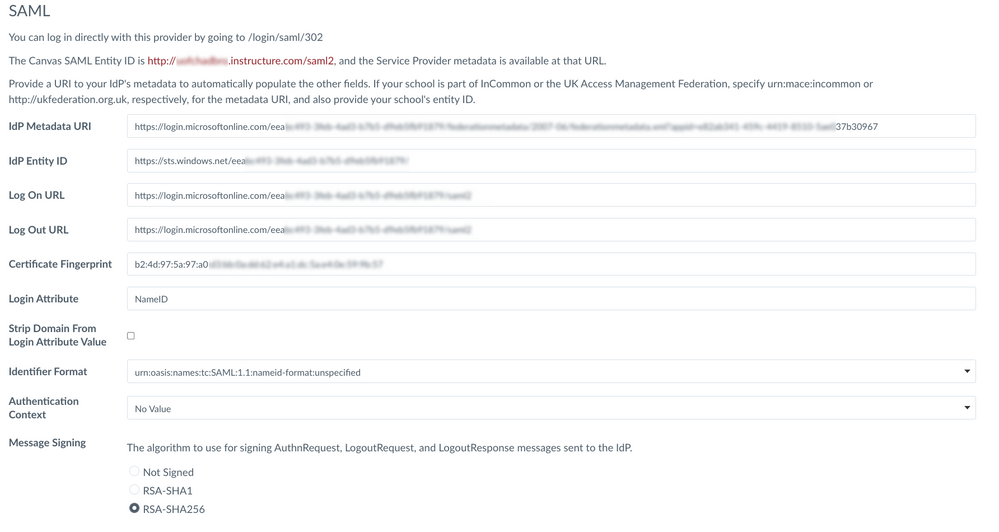
15. On the SAML configuration page, paste the App Federation Metadata Url into the IdP Metadata URI field. Click Save.
16. The page will reload with the values for IdP Entity ID, Log On URL, Log Out URL and Certificate Fingerprint automatically filled.
17. Test the configuration. Open a new incognito window, and go to
https://<YOURDOMAIN>.instructure.com/login/saml
If successful, you will be prompted to enter your Microsoft email address, followed by your password. You will then be logged in and redirected to your Canvas instance.
***NOTE: Canvas does not automatically create user accounts from successful single-sign-ons. User accounts must either be created manually in the web interface or through the SIS import CSVs.
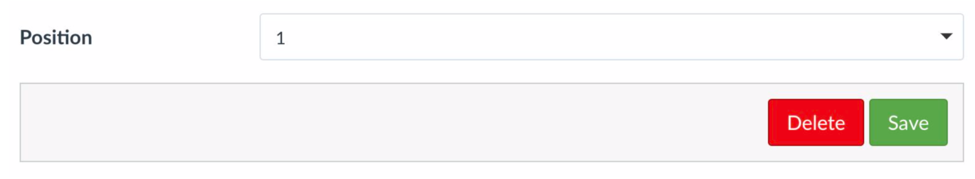
18. Return to the Authentication screen. To make SAML the primary method for authentication, navigate to the bottom of the SAML section, and change Position to 1. Click Save.
Congratulations! You have configured Microsoft Entra ID inside Canvas LMS
Have a question about Canvas? Ask in the Q&A forum:
Embed this guide in your Canvas course:
Note: You can only embed guides in Canvas courses. Embedding on other sites is not supported.
 Community help
Community help
To interact with Panda Bot, our automated chatbot, you need to sign up or log in:
Sign inView our top guides and resources:
Find My Canvas URL Help Logging into Canvas Generate a Pairing Code Canvas Browser and Computer Requirements Change Canvas Notification Settings Submit a Peer Review AssignmentTo interact with Panda Bot, our automated chatbot, you need to sign up or log in:
Sign in