Configuring Okta (SAML) and Canvas Authentication
|
Official Canvas Document |
|
Authentication Terminology
| Term | Definition |
|---|---|
| IdP |
Identity Provider The job of the IdP is to identify users based on credentials. The IdP typically provides the login screen interface and presents information about the authenticated user to service providers after successful authentication. Okta is the Identity Provider. |
| login_id |
Username in Canvas terminology. When information about an authenticated user is returned to Canvas, a user with a login_id matching the incoming data is looked for. |
| Metadata |
Information about the SP or IdP. This metadata is almost always provided in the form of XML. The metadata about your Canvas instance is located at https://<YOURDOMAIN>.instructure.com/saml2 (replace <YOURDOMAIN> with the first portion of your Canvas domain). |
| SAML |
Security Assertion Markup Language |
| SIS | Student Information System |
| SIS ID |
Unique ID of a user in Canvas. Used to link a user to an outside system, often a Student Information System (SIS). |
| SLO |
Single Logout When a user logs out of a service, some IdPs can subsequently log the user out of all other services the user has authenticated to. Okta supports this but may occasionally experience issues such as preventing a successful logout. Users will be logged out of Canvas but may not be logged out of Okta. |
| SP |
Service Provider An SP is usually a website providing information, tools, reports, etc to the end user. Canvas provides a learning environment to teachers, students, and admins and is, therefore, the Service Provider. Note: An SP cannot authenticate against an IdP unless the IdP is known to the SP. Likewise, an IdP will not send assertions to an SP that it does now know about. |
| SSO |
Single Sign-On This is what happens when a user isn't required to log in to a second service because information about the authenticated user is passed to the service. |
Pre-requisites
- Canvas does not automatically create user accounts from successful Single sign-ons (SSO) (unless "Just in Time Provisioning" is selected in the SAML configuration). User accounts must either be created manually in the web interface or through the SIS import CSVs.
- The login_id field in Canvas must match the selected field returned from Okta.
- Your organization must have an Okta subscription.
- You must be able to login to the Okta admin console for your organization.
- Referencing of <YOURDOMAIN> in this guide is referring to your Canvas URL (ex: https://<YOURDOMAIN>.instructure.com would be https://institution.instructure.com)
Login Release Valve
You may accidentally lock yourself out of Canvas while you are setting up authentication. If this happens, you can log in to Canvas using local authentication. Simply go to:
This forces Canvas to display the local login form, rather than redirecting to the SAML login page.
Configure Okta
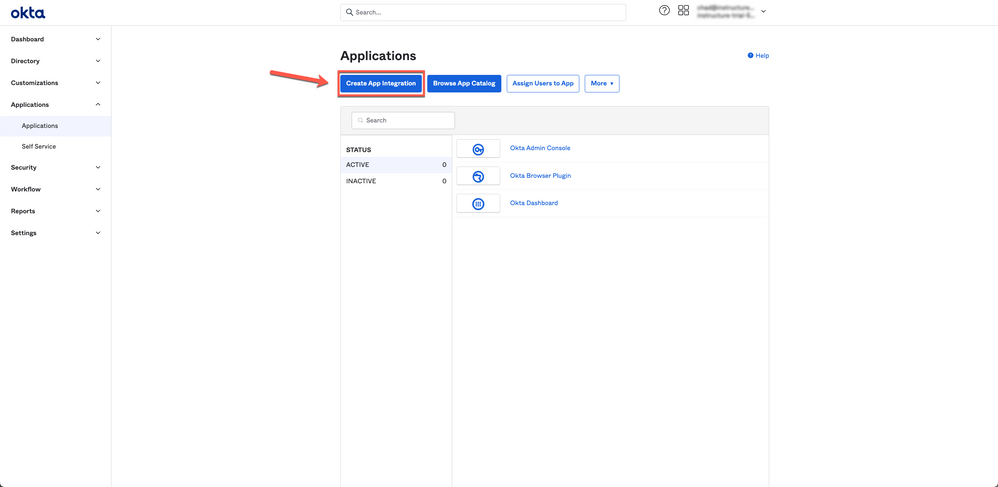
To configure Canvas authentication through Okta, you will need to create a SAML 2.0 application integration.
-
As an Okta admin, access the Application menu. Click the Applications
- Click Create App Integration
-
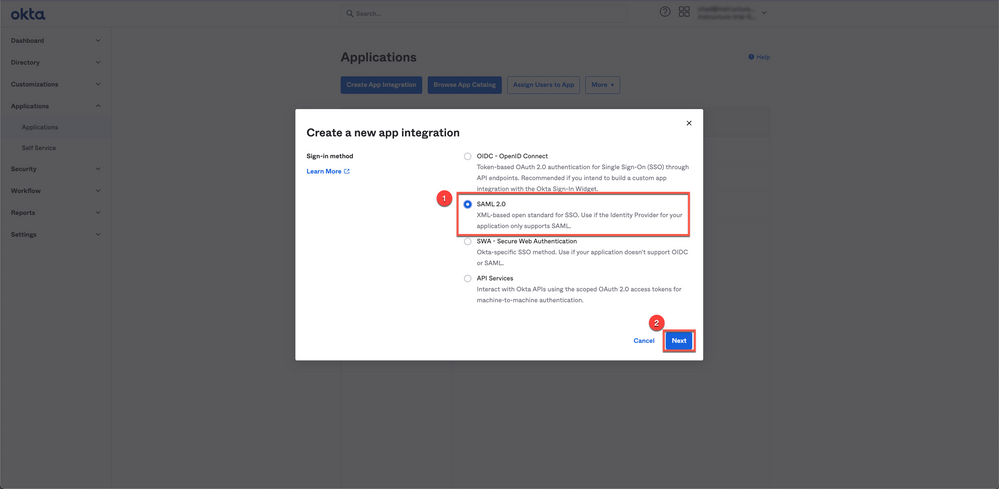
In the Create a New App Integration window, select:
-
Sign-in method: SAML 2.0 [1]
Then click the Next button [2]
-
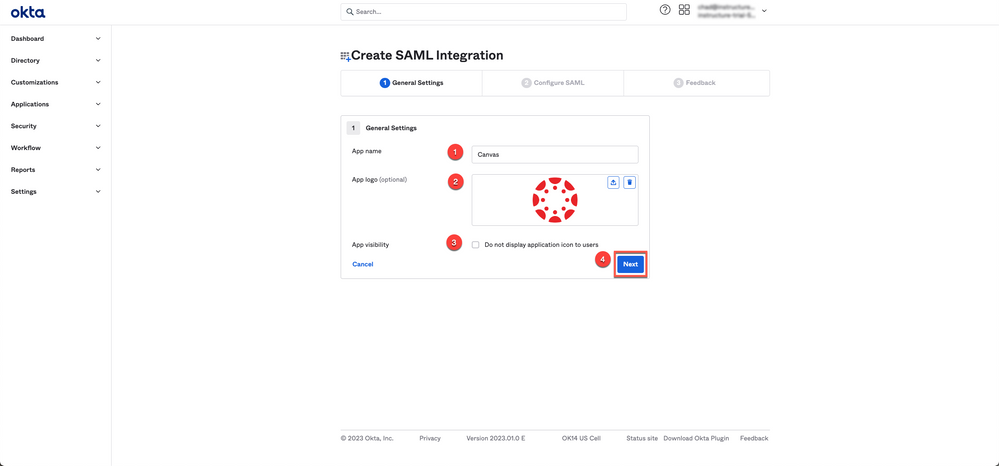
4. Enter an app name Canvas [1]. You may also upload a logo (optional: branding files) [2] and configure app visibility per your organization’s preferences [3]. Click the Next button
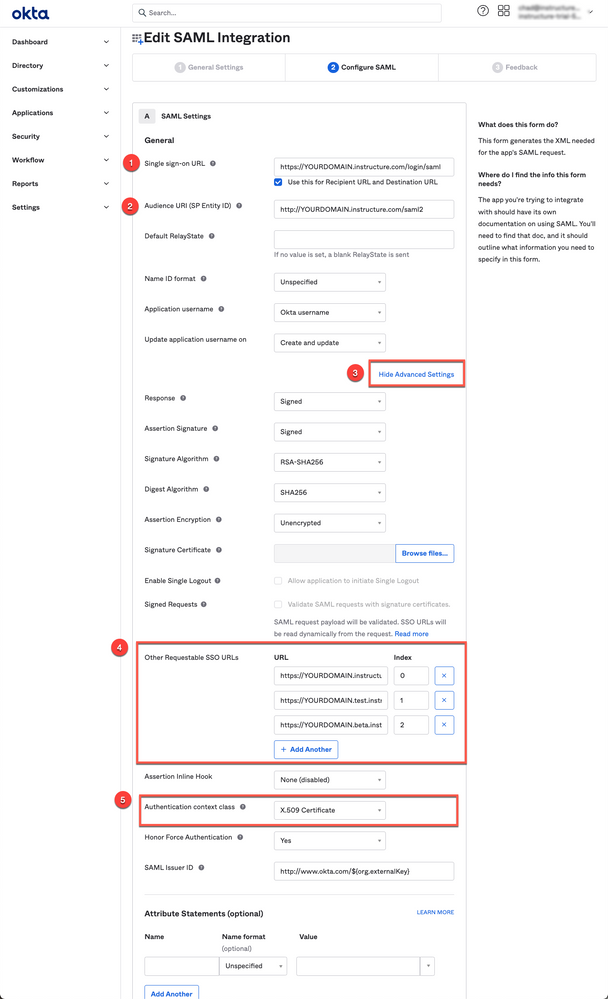
5. Configure SAML settings:
Single sign-on URL: https://<YOURDOMAIN>.instructure.com/login/saml [1]
Audience URI (SP Entity ID): http://<YOURDOMAIN>.instructure.com/saml2 [2]
(Note: use HTTP, not HTTPS in this field)
Click Show Advanced Settings [3]
Enter Other Requestable SSO URLs (configure your Canvas Production, Test, and Beta environments) [4]
https://<YOURDOMAIN>.instructure.com/login/saml
Index: 0
https://<YOURDOMAIN>.test.instructure.com/login/saml
Index: 1
https://<YOURDOMAIN>.beta.instructure.com/login/saml
Index: 2
Important: Make sure the "Authentication Context Class" is set to X.509 Certificate [5]
At the bottom of the page, Click the Next button
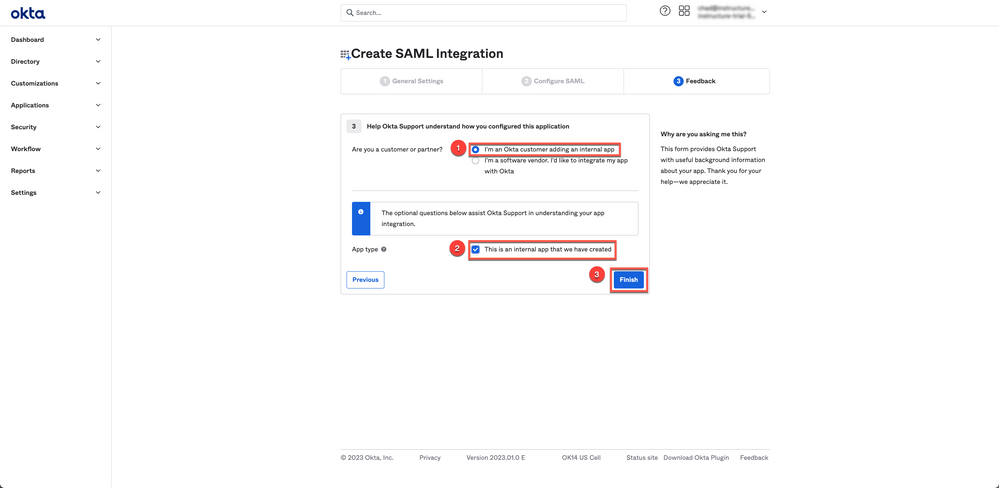
6. Select the I'm an Okta customer adding an internal app option [1] and check the box This is an internal app that we have created [2]. Then click the Finish button
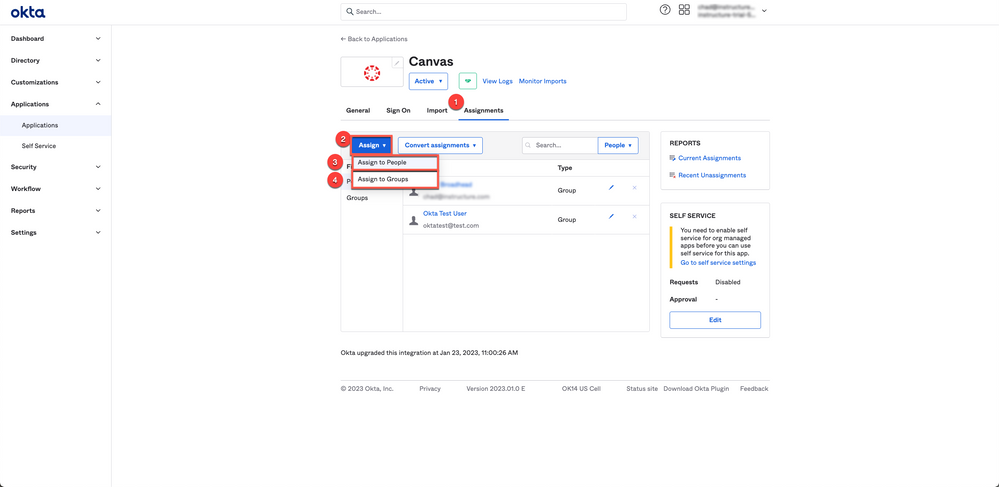
7. Assign people/groups to the new Canvas application. On the application, click Assignments [1], Assign [2], either individuals [3] or groups [4]. Then proceed with the selection.
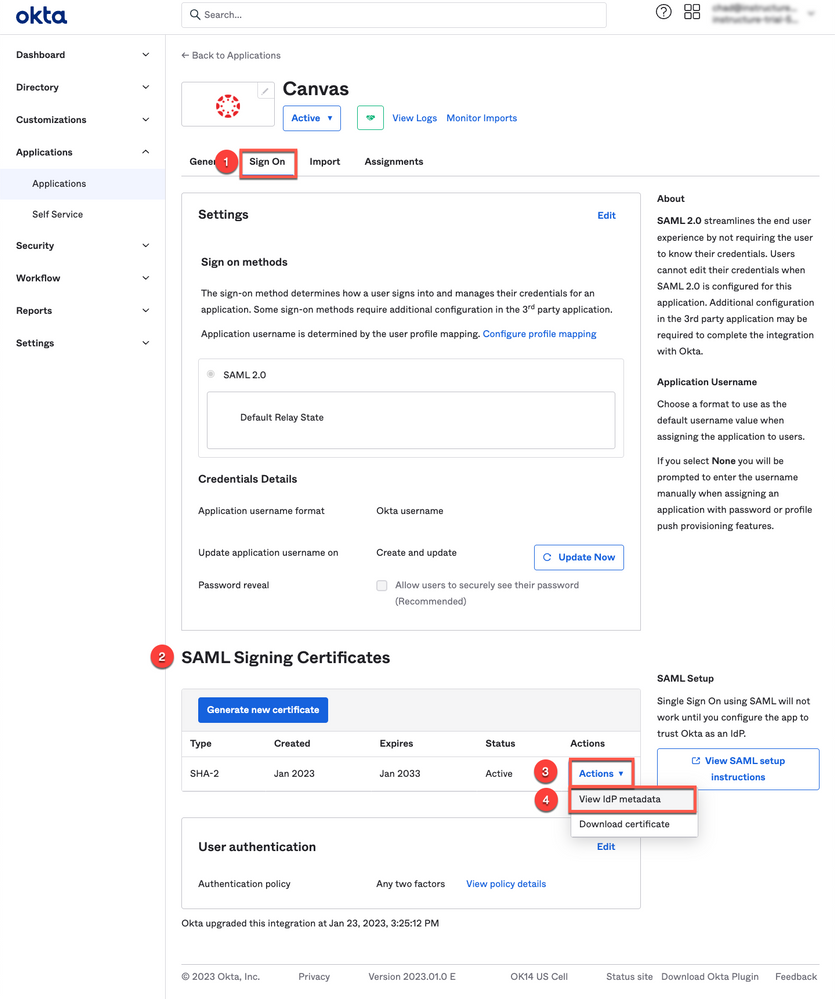
8. On the Sign On tab [1] of the application, under SAML Signing Certificates [2] click on Actions of the active certificate [3] and click View IdP metadata [4]
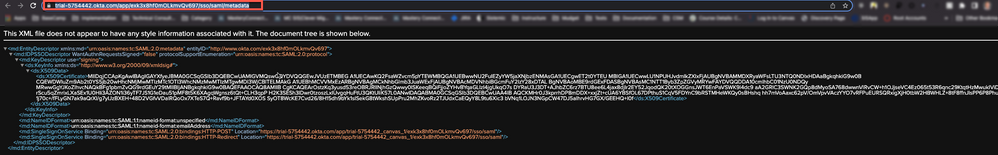
9. Copy the URL on the new tab displaying the IdP Metadata
Configure Canvas Authentication
The following steps take place in Canvas.
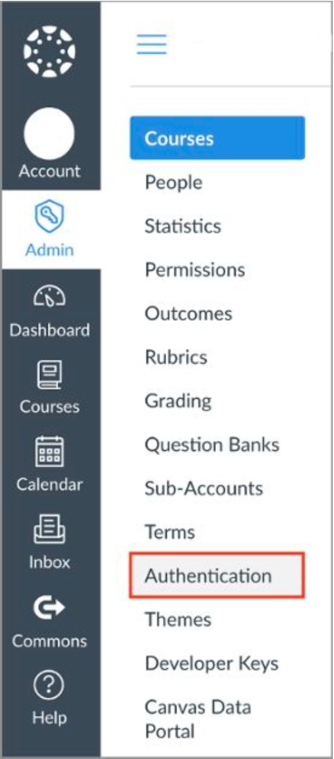
1. In a new browser tab, log in to your Canvas instance as an administrator. From the Admin tile, click Authentication
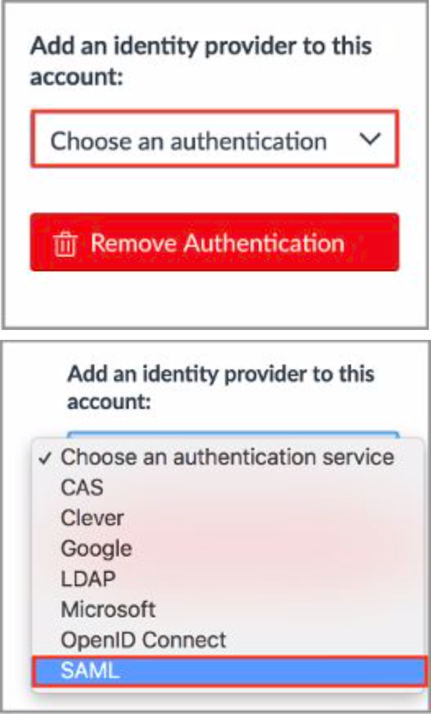
2. Click on the Choose an Authentication drop-down, then select the SAML option
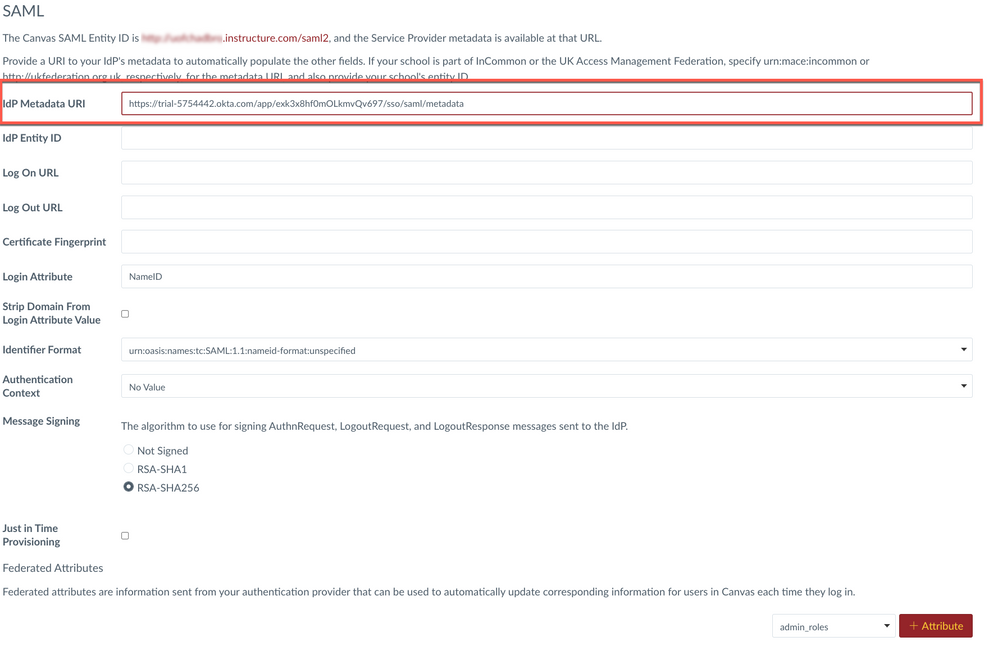
3. On the SAML configuration page, paste the Identity Provider metadata URL (from step 9 above) into the IdP Metadata URI field. Click Save
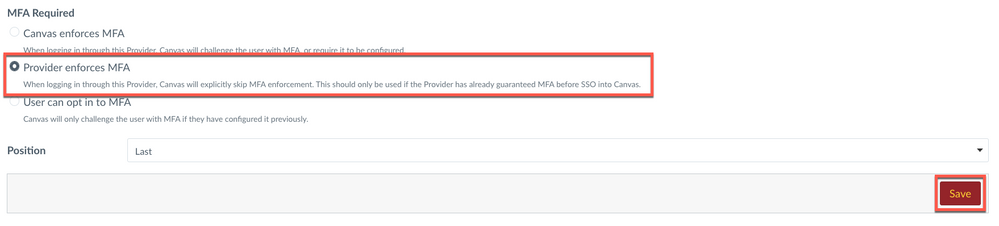
3a. Optional Setting (MFA): If your institution has turned on MFA in the account settings, follow the next steps. Select Provider enforces MFA MFA setting meaning the IdP will enforce MFA (even if it does not). The other MFA settings are Canvas-related. Click Save
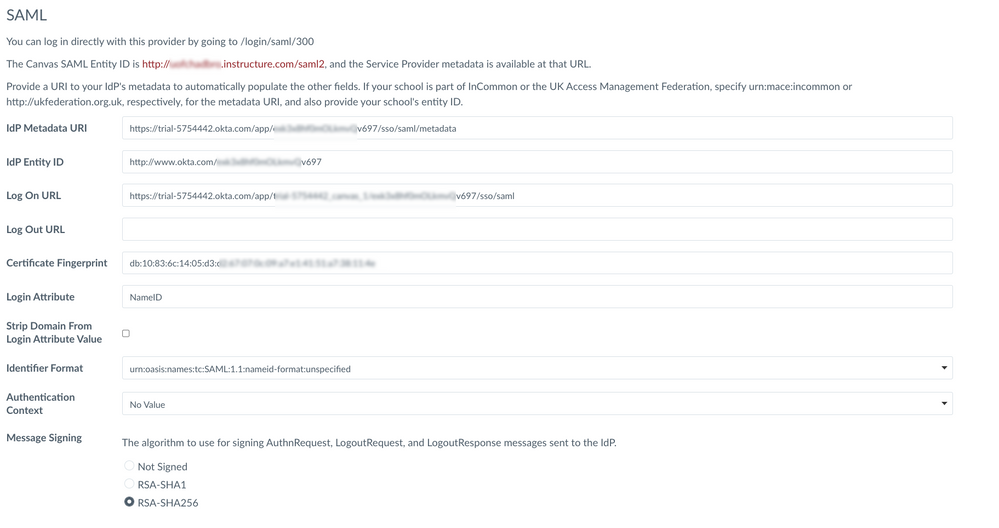
4. The page will reload with the values for IdP Entity ID, Log On URL, Log Out URL and Certificate Fingerprint automatically filled (example below)
5. Test the configuration. Open a new incognito window, and go to
https://<YOURDOMAIN>.instructure.com/login/saml
Or if multiple SAML configurations are configured, find the URL that is specific to that configuration
https://<YOURDOMAIN>.instructure.com/login/saml/<number>
(from the screenshot above in step 4, we can see that the login is /login/saml/300. The URL would then be https://<YOURDOMAIN>.instructure.com/login/saml/300)
If successful, you’ll be prompted to enter your Okta email address and password. You will then be logged in and redirected to your Canvas instance.
Note: Canvas does not automatically create user accounts from successful single-sign-ons. User accounts must either be created manually in the web interface or through the SIS import CSVs.
Congratulations! You have configured Okta IdP inside Canvas